Evaluating file sync and share solutions: 12 questions to ask about security
Published on May 28, 2014
File sync and share can increase productivity, but how do you pick a solution that works for you? There will likely be a number of factors guiding your decision, and if you’re like most businesses, security is high on the list. Here are some important security questions to ask when evaluating file sync and share vendors.
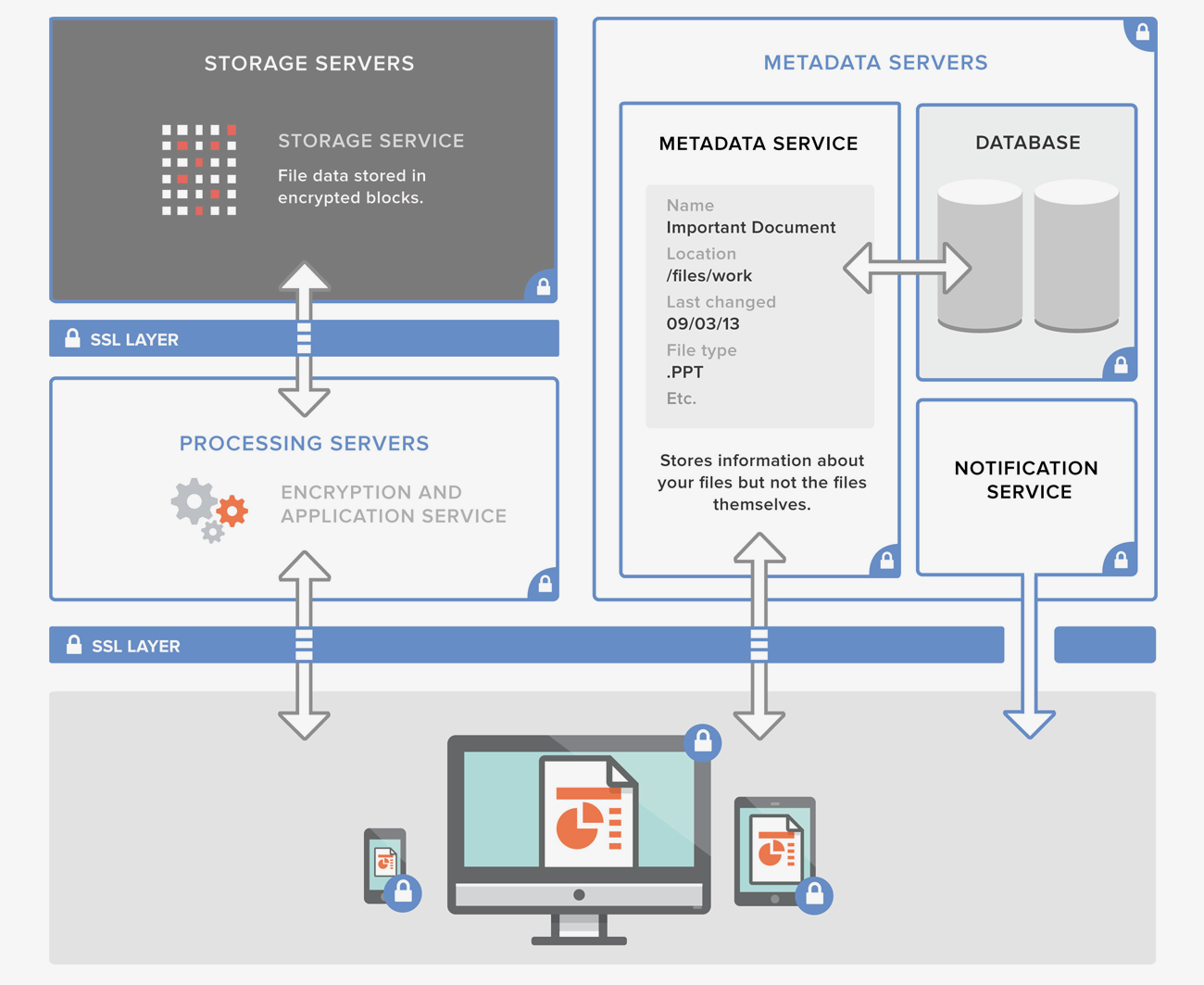
How is data encrypted? Consider this the first line of defense in protecting your company data. Be sure to find a solution that encrypts your data both “in transit” (as it moves between your company and the solution provider) and “at rest” (in the vendor’s storage). For regulated industries like healthcare or government, or if you’re looking for additional security, you may also want to ask if client-side encryption is available, either from the vendor or via third-party software.
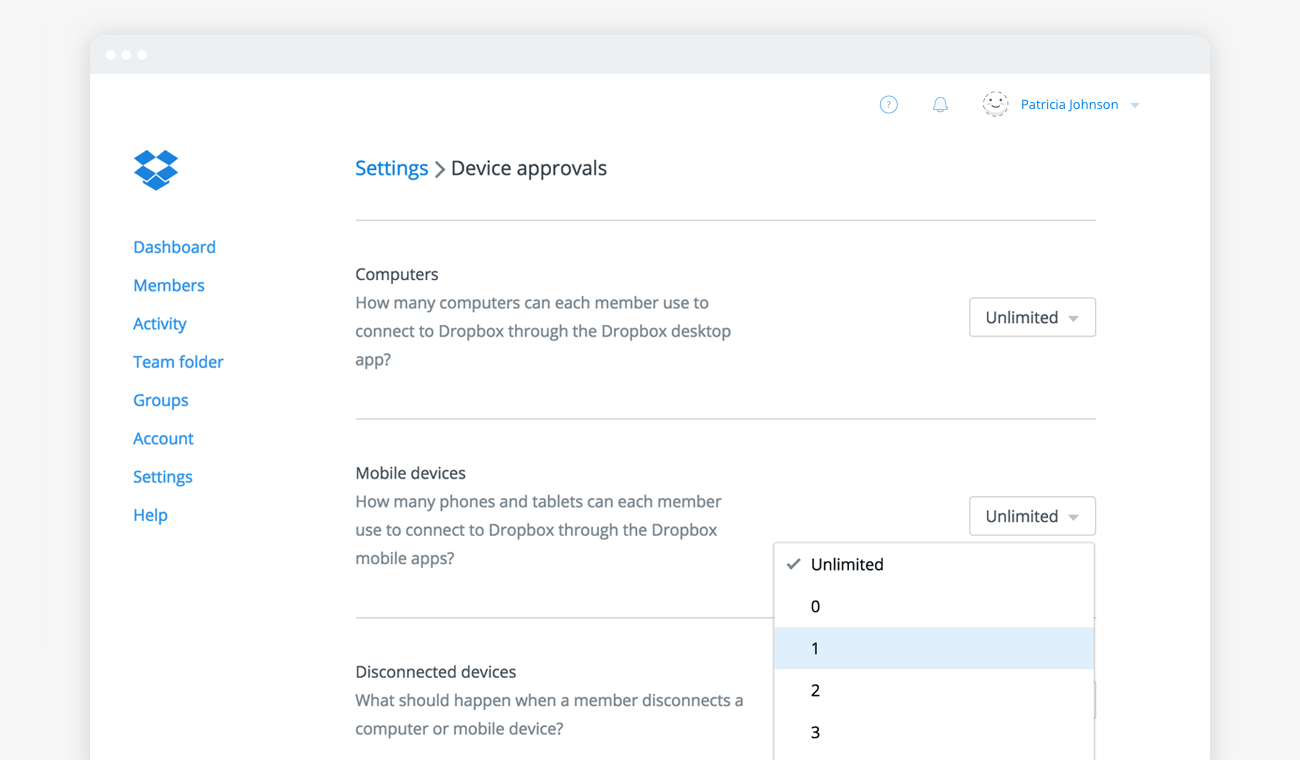
Is two-step verification supported? This increasingly common security feature offers additional protection when logging in. When enabled, the product will require a one-time-use security code — delivered via text message, phone call, or authentication app — in addition to a password upon sign-in.
What kind of reporting is available to admins? With file sync and share solutions making information more accessible and shareable, auditing the flow of data is crucial. Logs and exportable activity reports help your IT team keep tabs on who’s accessing your data and how they’re doing so.
Is single sign-on (SSO) supported? This feature streamlines management of multiple services and, perhaps more importantly, applies your corporate network’s password policies to all integrated services. In addition to the industry-standard SAML protocol, many services will offer SSO integration through third-party identity management solutions.
Can data be remote wiped? This feature allows admins to delete copies of data stored on an employee’s device if it’s lost, or when the employee leaves the team. Some solutions even allow non-admin users to delete data on their own devices, which is a good way to quickly lock down data immediately after a smartphone goes missing.
Can web sessions be terminated remotely? One of the draws of file sync and share solutions is anywhere, anytime access, which for many users means logging in from someone else’s computer. In cases where people have forgotten to log out when they’re done, the ability to quickly plug the security hole by terminating the session from another computer is invaluable.
What kind of permissions control is available? The ability to limit access to files, folders, or even entire accounts can be important to businesses, and current file sync and share solutions offer varying degrees of control. When looking at these controls in a given product, think about how user-friendly they are, and how likely people will be to use them in their daily workflow. After all, controls are only effective when they’re actually implemented.
If third-party apps can access data, how is authentication handled? It’s important that third-party apps are only granted access to data, and never to account credentials. Industry standards such as OAuth provide a way for users to maintain the security of their accounts, while allowing them to access their data through a broader variety of tools.
To what degree can the vendor access my company data? Most file sync and share providers will have strictly enforced policies restricting customer data access to a small subset of their employees. This access should be clearly defined and only allowed on an as-needed basis. Be sure to get the details of these policies from any vendors you’re considering.
What compliance certification and auditing has the vendor completed? You're thinking about entrusting someone with possibly mission-critical business data, so don't just take vendors’ word for it; look for independent authorities to validate their policies. Service Organization Control (SOC) auditing, which examines a service organization and its internal controls, and ISO 27001 certification, which sets standards for information security management, are particularly relevant to providers of file sync and share solutions.
What does the vendor do to protect user privacy? With data privacy becoming a growing concern for both individuals and businesses alike, it’s up to solutions providers to communicate their stances and policies. Ask vendors for a privacy policy that clearly articulates how your information is managed, as well as information on how government data requests are handled.
How does the vendor protect its own data? Like it or not, your data and your vendor’s are inextricably linked. Any weaknesses in your vendors’ systems can be used to access your data just as much as theirs. Finding a vendor with clearly established policies for protecting their physical infrastructure is critical.
Finally, it's always important to ask, "Will my users choose to use this solution?" These days, more and more documents are created outside the traditional corporate firewall, so a key part of keeping business data secure is making sure employees actually use the company-approved file sync and share solution to begin with. That's why user adoption is a key consideration when evaluating vendors — because no matter how secure a service is, it can't protect data it never sees.
Want to learn more about how Dropbox for Business handles security? Check out our security features here.