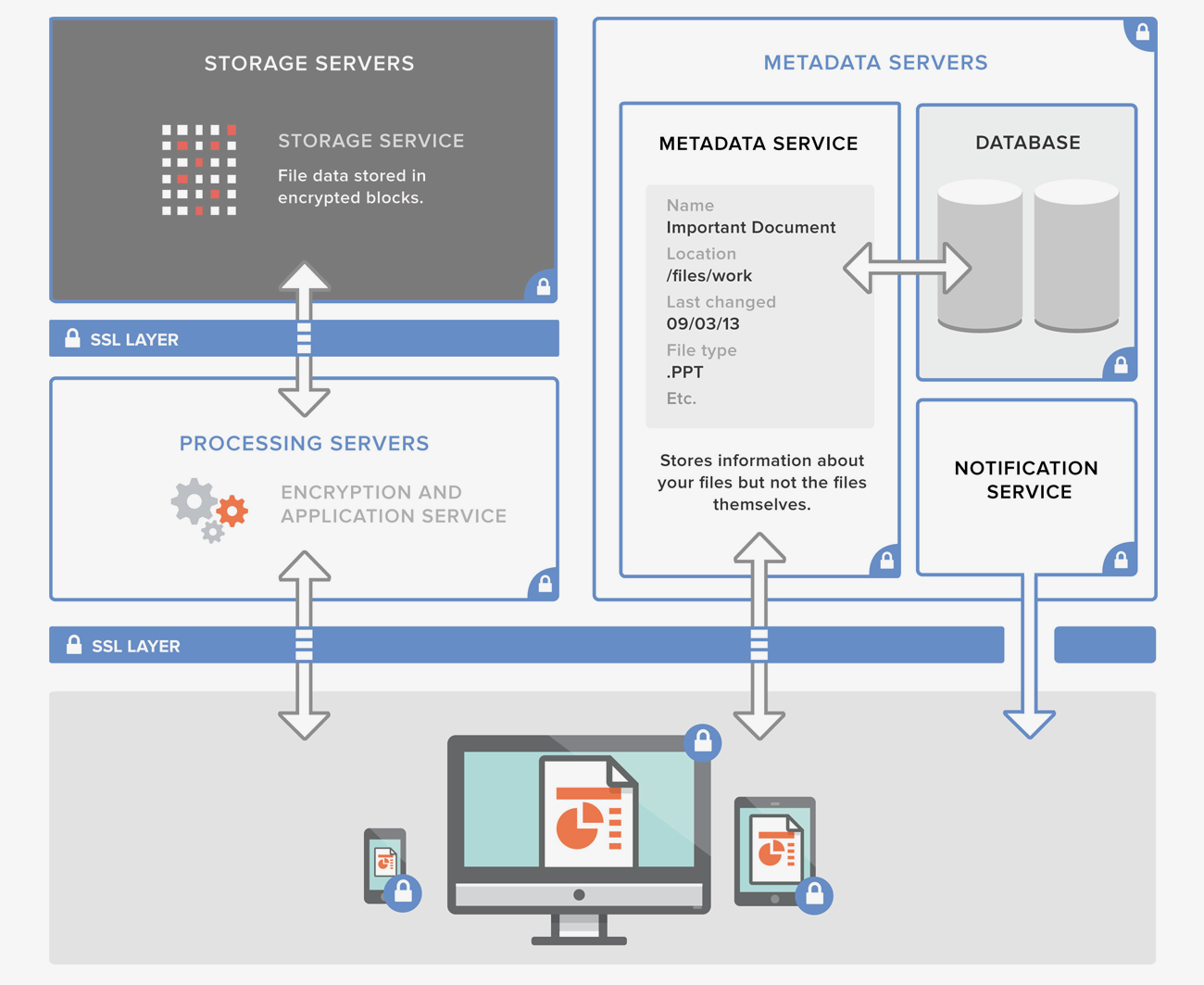
“Security” is the number one issue holding business leaders back from the cloud. But does the reality match the perception? Keeping data close to home, on premises, makes business and IT leaders feel inherently more secure. But the truth is, cloud solutions can offer companies real, tangible security advantages. Before you assume that on-site is the only way to keep data safe, it’s worth taking a comprehensive approach to evaluating risks. Doing so can lead to big benefits.
Giving up physical possession doesn’t mean you’re giving up security. Good solutions, whether they’re on premises, part of a hybrid cloud, or a public cloud like Dropbox, are an extension of your network and the security infrastructure you already have in place. Deployed properly, businesses can see many tangible benefits from public cloud solutions including increased productivity, integration with existing systems, and cost savings. That said, it's important to understand the real security threats out there and how to approach security for cloud-based solutions. Here’s the nitty gritty of why and how.
What are the real risks?
To get to the root of people’s concerns, we need to understand the threats. Let’s start with the physical location of your data. Physical theft, employee mistakes (like lost devices), and insider threats are responsible for 42.7% of 2013 data breaches in the US, according to Privacy Rights Clearinghouse. Computers, laptops, and company servers are responsible for the large majority of your vulnerabilities, not the cloud.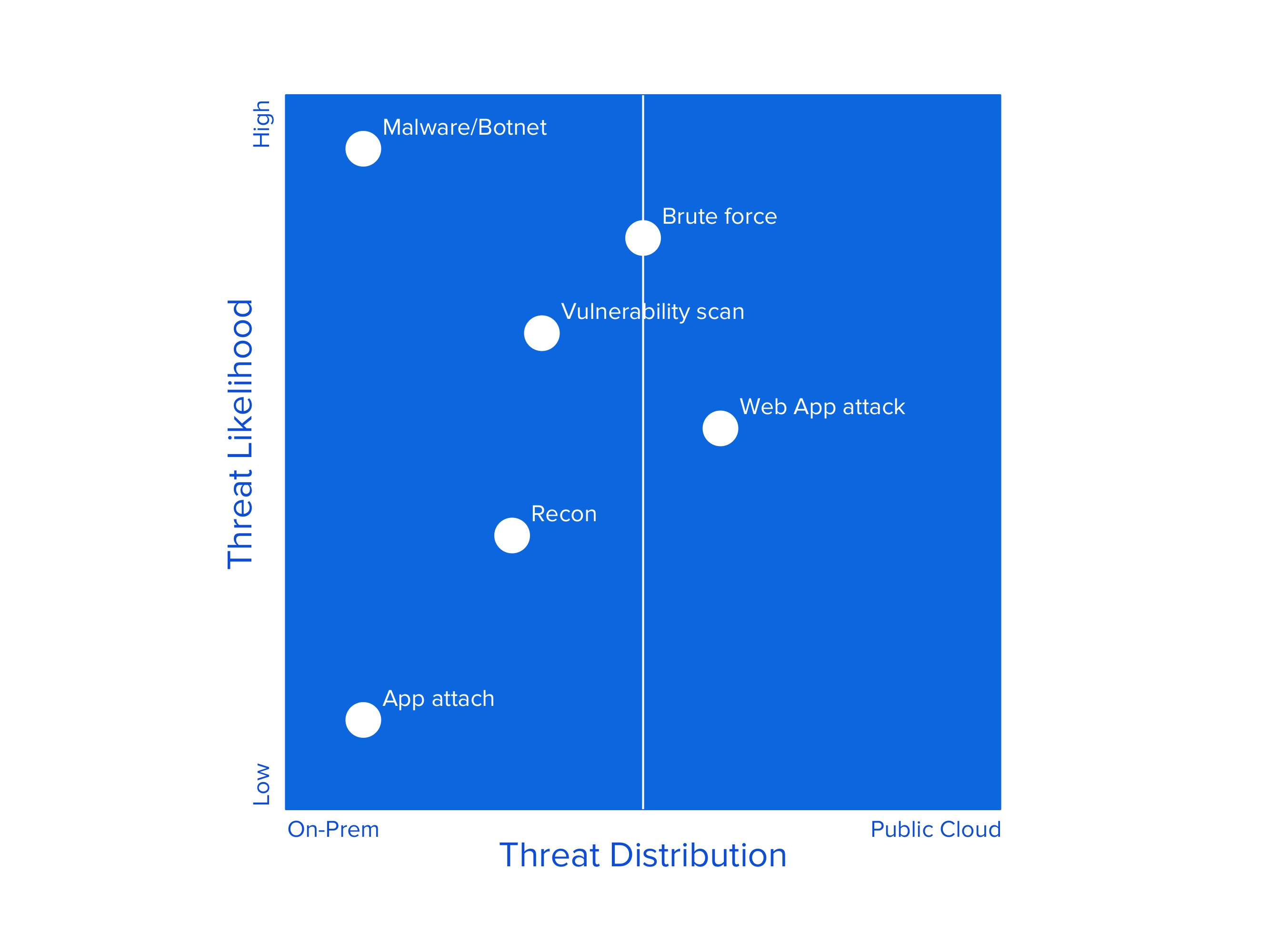
In another 29.6% of data breaches, hackers broke into data owned by companies and government agencies. Big tech companies, major retailers, and airlines were among the 2013 victims. Let’s take a closer look at what these kinds of hacks look like and how they’re distributed.
Alert Logic, an IT services provider, publishes a semi-annual State of Cloud Security report, surveying their customers to understand where security threats are coming from. The results are interesting:
-
An enterprise data center (EDC) is 4x more likely to suffer a malware/bot attack than a cloud hosting provider (CHP).
-
EDCs and CHPs are equally vulnerable to a “vulnerability scan” and a “brute force” hack.
-
EDCs are 3x times more likely to suffer a recon and 4x an app attack.
Where are cloud providers more vulnerable? They’re 40% more likely to suffer a web app attack and 10% more prone to a vulnerability scan weakness than an enterprise data center. In recons, malware, bot, and app attacks, the cloud seems to have less risk than on-prem. The takeaway isn’t that the cloud is better. It’s that no one — regardless of their resources — is 100% secure, but everyone strives to get as close as possible. It’s all about how you manage those risks.
What security benefits can the cloud offer you?
Cloud-based solutions can offer you some significant security advantages. First, services like Dropbox make security their top priority. We have to. It’s like putting your money in a bank. Making sure that money stays safe is the bank’s number one priority, or they won’t have a business. The same holds true for any cloud service. Trust takes years to build, but can be lost in seconds.
That deep commitment to security means we have to invest far more in scalable infrastructure and information security than most organizations. Those investments are quite significant, and we bear that burden for you. We can create economies of scale and efficiencies that benefit you.
Think about it like this: services like Dropbox go above and beyond to protect your data — so that you don't have to invest heavily in secure systems and servers, constantly consider network and product security threats, submit to in-depth compliance reviews and audits, undergo regular testing against attacks, set up complex logical access controls, and assure data centers have advanced physical, environmental and operational security measures.
How should you approach information security?
Hopefully it’s clear why the cloud has some advantages. But how do you evaluate whether those advantages are right for you?
-
Recognize your real needs: Understand what your data security and governance requirements are and should be. Establish realistic, grounded expectations around the level of security and control you need and want. Make sure you know what problems you’re trying to solve. Don’t ask for the Fort Knox of security systems if it’s not what you really need, or you’ll end up spending more money, time, and resources than you should.
-
Remember the user: Look beyond traditional security measures to usability and adoption. If your employees won’t use the solution, there’s no point in implementing it, no matter how secure it may appear to be. And when employees start using workarounds that you have little control over, you’ll find they pose a much bigger security risk.
-
Worry less about location: Keep an open mind. The security of your data is more important than its location. A distributed information storage infrastructure is secure by design, and certainly more so than keeping all your info unencrypted in a single location. Storing data remotely guarantees data redundancy, easy access no matter where you are, and scalability with no impact on performance and speed.
-
Focus on access: Remember that controlling access is key. Look at how your data is accessed, and look specifically at holes that could be exploited. Most data breaches occur by finding vulnerabilities and poor end user practices, regardless of whether your information is cloud-based or on premises. Make sure your employees aren’t making common mistakes like reusing passwords. Ensure that you’ve configured devices with appropriate encryption and set up a strong device management system.
-
Assure credibility: When evaluating a partner, check for certifications and compliance with recognized standards and frameworks, levels and types of encryption, and product features that give you control and visibility.
-
Invest in a 24/7 approach: Finally, make sure your providers are auditing, monitoring, and testing security on a continuous basis.
Security concerns shouldn’t hold you back from file sync and share providers like Dropbox for Business. It’s hard to find the time, resources, and knowledge necessary to defend against such an immense range of threats, so in many cases, it makes a lot of sense to let good, reputable cloud providers handle those issues for you. In the end, you can relieve headaches for IT, get more done, and focus on growing your business.
Check out the Dropbox for Business website to learn more about how we protect your important information.
Cory Louie is the Head of Trust, Safety, and Security at Dropbox. He formerly served as Head of Trust & Safety at Google. Before that, Cory was a Secret Service Special Agent, where he protected people but also specialized in network intrusions, unauthorized computer access, financial fraud, phishing, malware, and other Internet-based threats.