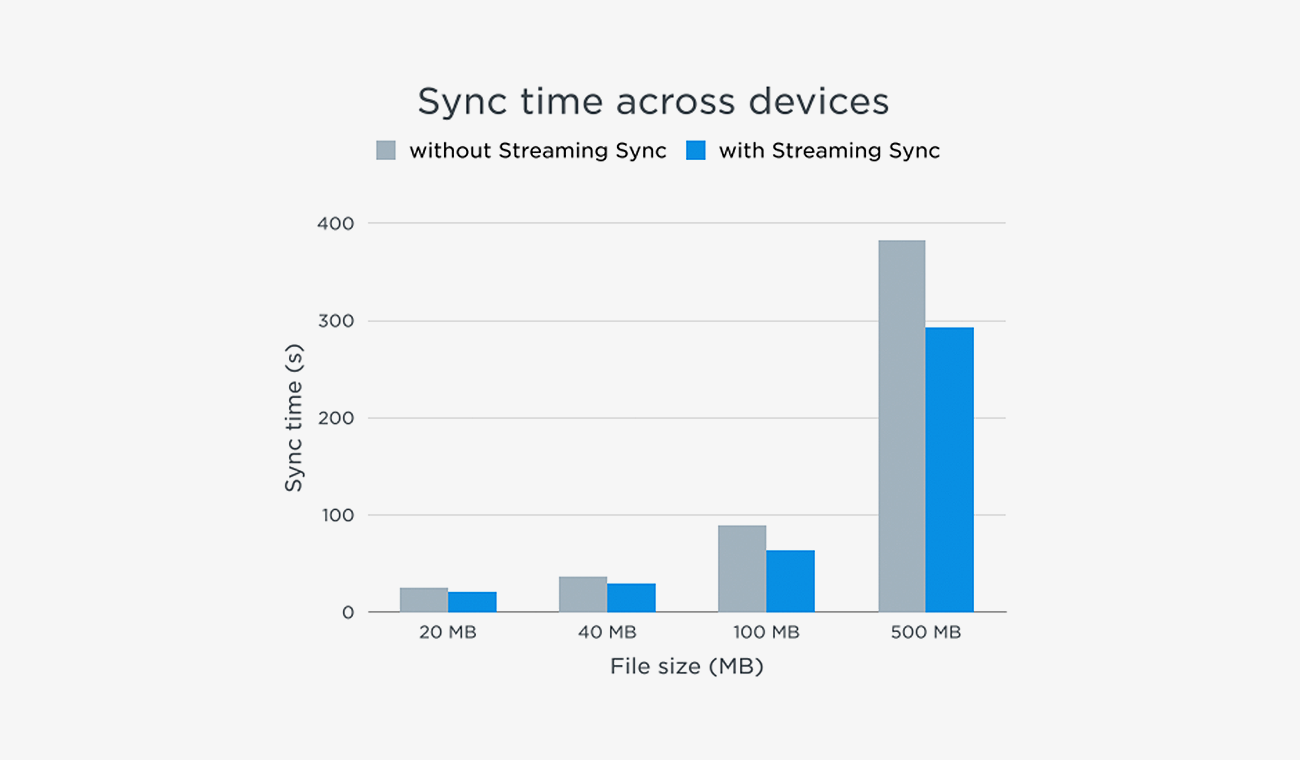
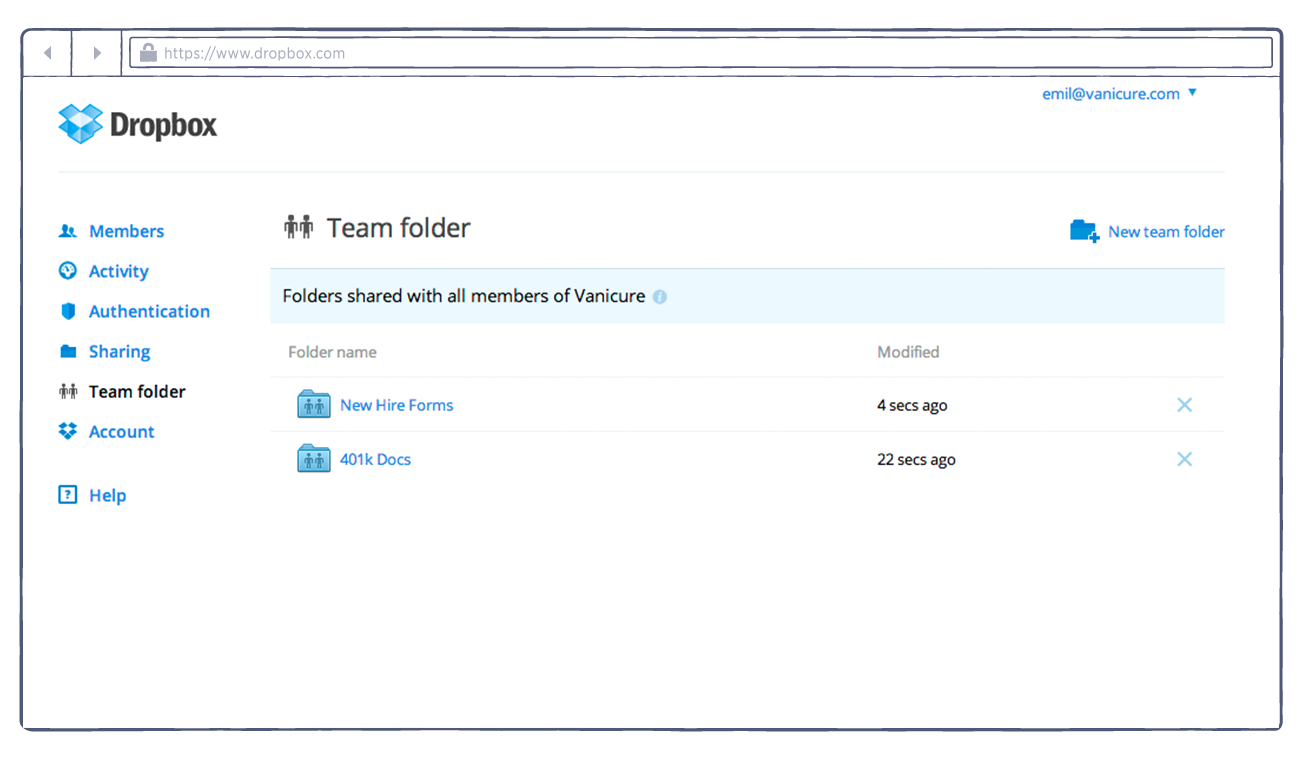
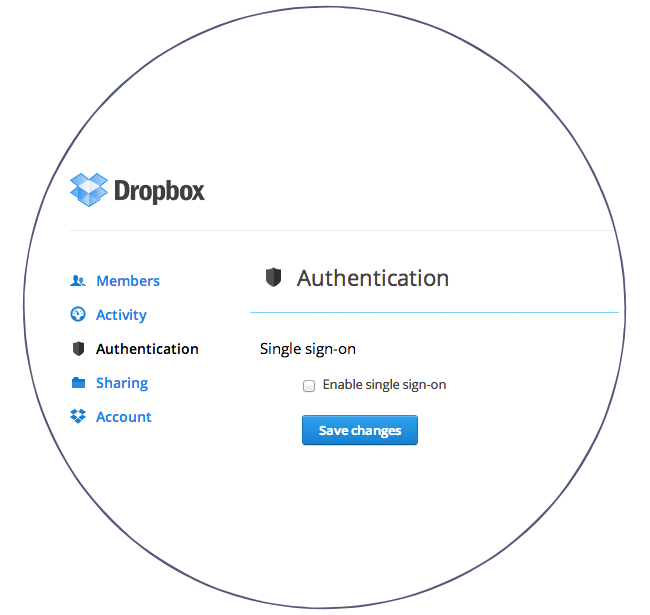
Compliance with Laws and Law Enforcement. Dropbox cooperates with government and law enforcement officials and private parties to enforce and comply with the law. We will disclose any information about you to government or law enforcement officials or private parties as we, in our sole discretion, believe necessary or appropriate to respond to claims and legal process (including but not limited to subpoenas), to protect the property and rights of Dropbox or a third party, to protect the safety of the public or any person, or to prevent or stop any activity we may consider to be, or to pose a risk of being, illegal, unethical, inappropriate or legally actionable.
New TOS:Compliance with Laws and Law Enforcement Requests; Protection of Dropbox’s Rights. We may disclose to parties outside Dropbox files stored in your Dropbox and information about you that we collect when we have a good faith belief that disclosure is reasonably necessary to (a) comply with a law, regulation or compulsory legal request; (b) protect the safety of any person from death or serious bodily injury; (c) prevent fraud or abuse of Dropbox or its users; or (d) to protect Dropbox’s property rights. If we provide your Dropbox files to a law enforcement agency as set forth above, we will remove Dropbox’s encryption from the files before providing them to law enforcement. However, Dropbox will not be able to decrypt any files that you encrypted prior to storing them on Dropbox.
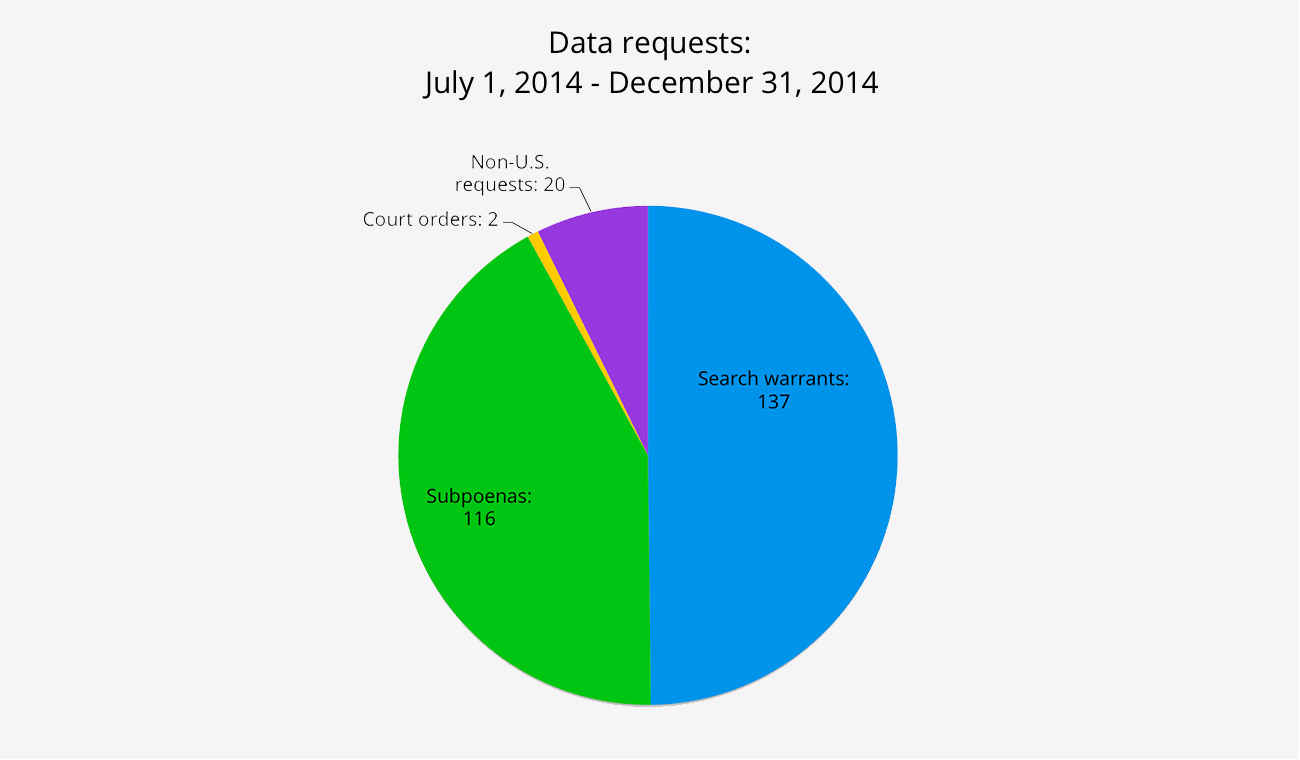
2. We comply with valid legal process and U.S. law The previous section should clarify our commitment to user privacy. That said, there have been a lot of questions raised about government data requests. Just so you know, we don't get very many of those requests -- about one a month over the past year for our more than 25 million users. That’s fewer than one in a million accounts. That said, like all U.S. companies, we must follow U.S. law. That means that the government sometimes requests us (as it does similar companies like Apple, Google, Skype, and Twitter) to turn over user information in response to requests for which the law requires that we comply. When we get a government request, we don’t just hand over your information or files. Our legal team vets all of these requests before we take any action. The small number of requests we have received have all been targeted to specific individuals under criminal investigation. If we were to receive a government request that was too broad or didn’t comply with the law, we would stand up for our users and fight for their privacy rights. 3. We protect the privacy of users and will provide notice of government requests for data whenever possible Our policy is to provide notice to users about law-enforcement demands for data, except in the event where the law or highly compelling circumstances prohibit us from doing so. 4. We have strict access controls that prohibit employee access to user data We know that millions of people rely on Dropbox to take care of their most important information. Keeping it safe and private is our top priority. Some concerns have been raised about our Help Center article and other statements that discuss employee access to user data. We agree that we could have provided more details and we will be updating these to make them more clear. Like most major online services, we have a small number of employees who must be able to access user data when legally required to do so. But that’s the exception, not the rule. We have strict policy and technical access controls that prohibit employee access except in these rare circumstances. In addition, we employ a number of physical and electronic security measures to protect user information from unauthorized access. 5. Encryption People have asked why Dropbox servers need to decrypt user data. The reason is many of the most popular Dropbox features -- like accessing your files from the website, creating file previews, and sharing files with other people -- would either not be possible or would be much more cumbersome without this capability. The files you store on Dropbox’s servers are encrypted using an industry standard, AES-256. We manage the encryption keys on our users’ behalf. This encryption protects against a variety of security threats, particularly when your data is at rest. For users who feel more comfortable managing their own encryption keys, we recommend using products like TrueCrypt to store encrypted volumes within their Dropboxes. Those users will unfortunately lose access to some functionality, but we leave this decision to the user. We believe that storing data in Dropbox is far more safe than the alternatives. We've designed Dropbox to protect user data against threats of all kinds, but we've focused on helping users avoid the most common threats: not having current backups, not having any backups at all, accidentally deleting or overwriting files, losing USB drives with sensitive information, leaving files on the wrong computer, etc. 6. We’re dedicated to security We’re proud of our excellent track record in security. Since the very beginning, we’ve devoted an incredible amount of resources and attention to it. We have always listened carefully to feedback from the community on things we can do to improve security. Over the past month, a couple of security concerns have been raised by the community. The first issue pertains to the security of our mobile applications. A report noted that our mobile applications were transmitting some metadata unencrypted. We made this decision to provide better performance (in our testing, enabling SSL for all metadata transfers made the app several times slower). We’ve listened to these concerns, and are working on a faster way to transmit metadata over SSL on the mobile apps. The second issue involves the security of a Dropbox account on a computer that's hacked or compromised. Unfortunately, when something like this happens, all applications and data on the computer are at risk. That said, we have developed ways to provide greater protection for Dropbox accounts on compromised computers. For example, last week's update to the Dropbox desktop app sets more restrictive permissions on the folder that stores the authentication file, and we will soon provide a solution that will make the authentication file useless on a second computer. 7. Talking about security We'd also like to address recent reports about our security and privacy policy that we feel are misleading and inaccurate. We openly discuss how Dropbox security works. Part of our challenge is that we have to communicate with people both familiar and unfamiliar with the intricacies of encryption and online security. Most of our users are learning about these issues for the first time, and rely on us to communicate in plain language about topics that are nuanced and complex, even for security professionals. We strive to communicate clearly and precisely about these issues. In this effort there's always a tradeoff between simplicity and exhaustiveness. For example, one help article formerly stated that "files stored on Dropbox servers are encrypted (AES-256) and are inaccessible without your account password." We were explaining that there are multiple safeguards on your data: that the files are stored encrypted and in addition, protected by your access credentials. However, a security professional could incorrectly infer that the encryption key comes from the user's password, so we've separated the two points for clarity. Another statement read “Dropbox employees aren’t able to access user files.” That means that we prevent such access via access controls on our backend as well as strict policy prohibitions. That statement didn’t say anything about who holds encryption keys or what mechanisms prevent access to the data. We updated our help article and security overview to be explicit about this. We will continue to try to find the right balance between using clear language and providing the right level of technical detail. And when we oversimplify something or the community asks for clarification, we do our best to respond directly and publicly. Over the years we've also responded in detail to users' questions about security. For example, we've routinely explained how we manage encryption keys on our users' behalf:- http://forums.dropbox.com/topic.php?id=36&replies=11#post-321 (2007)
- http://forums.dropbox.com/topic.php?id=312&replies=8#post-1539 (2008)
- http://forums.dropbox.com/topic.php?id=7421&replies=14#post-47812 (2009)
- http://forums.dropbox.com/topic.php?id=13907&replies=6#post-96927 (2010)



.png/_jcr_content/renditions/hero_square%20(1).webp)




.jpg/_jcr_content/renditions/1200x628%20(8).webp)































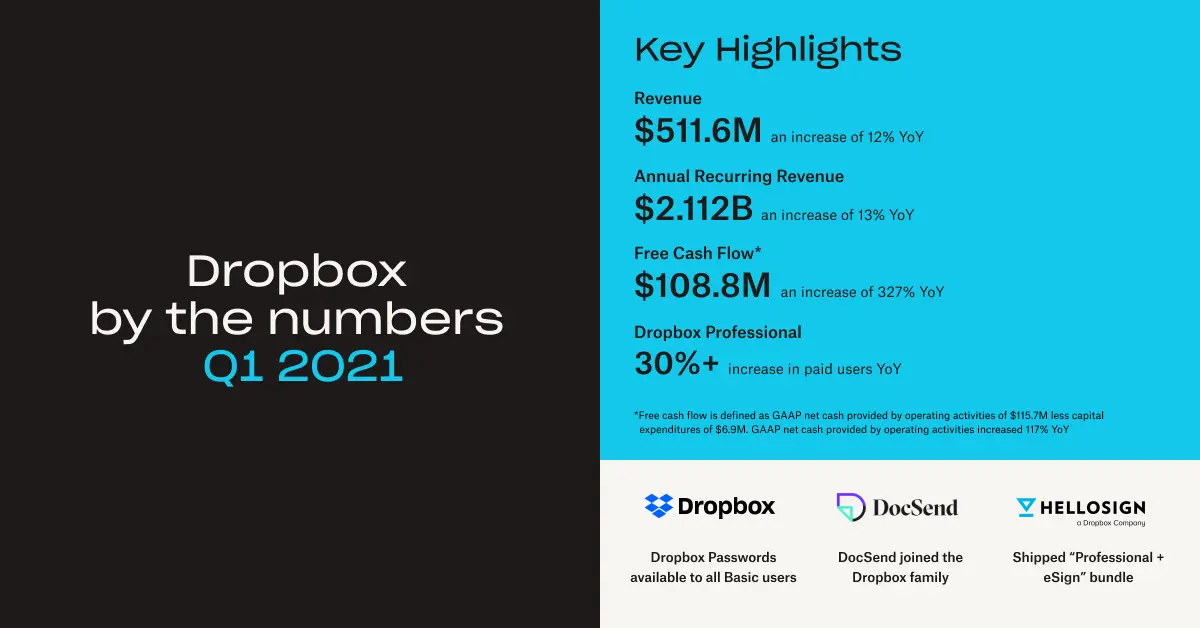









.png/_jcr_content/renditions/blog_(960x960).webp)